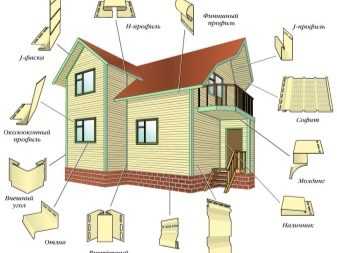
Ремонт – это больная тема большинства владельцев загородных домов и квартир. Зачастую требуется много вложение средств и сил, чтобы придать комнатам стильный современный вид. Не знаете, как сделать ремонт в квартире своими руками недорого и быстро? Замена окон, покраска потолка, переклеивание обоев, покрытие пола — всё это можно сделать без посторонней помощи быстро и недорого. При правильном подборе материалов и приложении чуть больших усилий можно сделать качественный и красивый ремонт с современной отделкой.

Советы по выбору правильного покрытия для стен, пола и потолка, а так же их монтаж и нанесение своими руками

Что бы сделать красивый и современный декор для дома своими руками, предлагаем посмотреть фото готовых решений в статье и мастер-классы.
С чего начать недорогой ремонт
Участок, которые требует участия специалиста при необходимости ремонта или замены, это электричество. Самый экономный вариант в этом случае, это вызов специалиста. Установка розеток в квартире может осуществляться без его помощи. Инструмент для ремонта в квартире дешевле всего брать напрокат.